Introduction
Cloud environment security is becoming crucial as cloud computing rapidly expands globally. This article will discuss
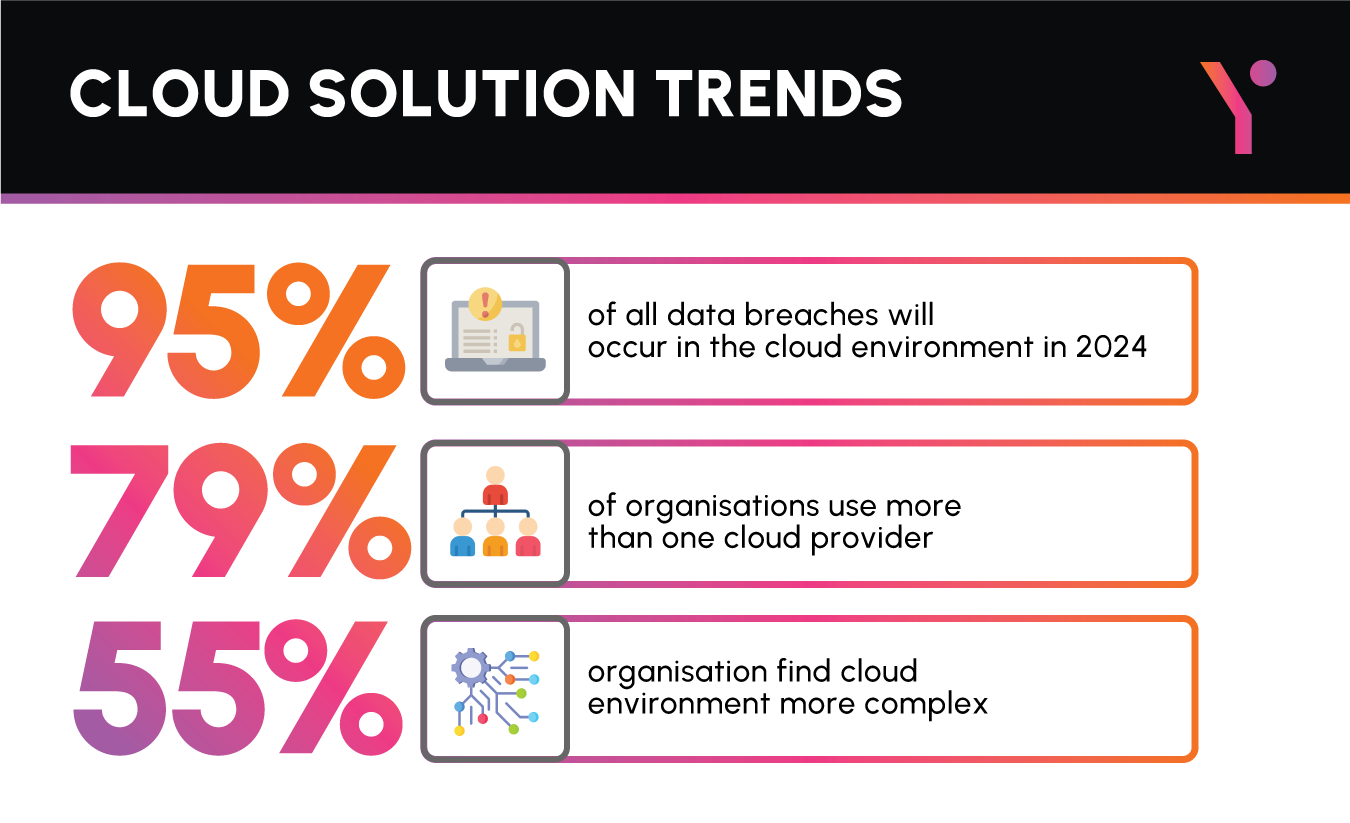
According to the 2023 Thales Cloud Security Study, 39% of organisations worldwide experienced a data breach in their cloud environment. This is an increase of 4% from last year. Data privacy on cloud environment is a growing concern and as the adoption rate of cloud environment rises organisations are looking for tools and solutions that can manage their cloud security.
According to stats by GlobeNewswire, the cloud computing market is expected to reach USD 2321.1 Billion by 2032, reaching a registered CAGR of 16% from 2023 to 2032. Cloud environments are a great way for organisations to improve efficiency in the daily processes, but along with the effectiveness, organisations also run the risk of data privacy threats.
In this article we will discuss the top 15 best Cloud Security Tools that you need to keep an eye out for in 2025 that can help protect your sensitive data within cloud environments and improve your cloud development services.
What Features Should You Look For In A Best Cloud Security Tool?
When selecting one of the best cloud security tool, several key features should be considered to ensure robust protection for your cloud infrastructure. You can also opt for a cloud technology consultancy to help you on your way to cloud automation.
Comprehensive Threat Detection
Look for a tool that offers advanced threat detection capabilities, including real-time monitoring, anomaly detection, and behaviour analysis to identify and mitigate security threats promptly.
Data Encryption
Ensure the tool provides robust encryption mechanisms to safeguard sensitive data both at rest and in transit. Look for support for industry-standard encryption protocols and key management practices to maintain data confidentiality.
Access Control and Identity Management
Choose a tool that offers robust access control mechanisms, including role-based access control (RBAC), multi-factor authentication (MFA), and identity federation to enforce granular access policies and prevent unauthorised access to your cloud resources.
Vulnerability Management
Select a tool that includes vulnerability scanning and assessment capabilities to identify security weaknesses and misconfigurations in your cloud environment. Look for automated scanning, prioritiation of vulnerabilities, and remediation guidance to address security risks effectively.
Compliance and Governance
Ensure the tool supports compliance with relevant regulatory standards and industry best practices. Look for features such as compliance reporting, audit trails, and policy enforcement to maintain regulatory compliance and adhere to security standards.
Incident Response and Forensics
Choose a tool that facilitates incident response and forensic analysis capabilities to investigate security incidents and breaches effectively. Look for features such as incident logging, incident notification, and forensic data collection to support post-incident analysis and remediation.
Integration and Orchestration
Select a tool that integrates seamlessly with your existing security infrastructure and cloud platforms. Look for support for common APIs, webhooks, and automation capabilities to streamline security operations and orchestrate responses to security events.
Scalability and Performance
Ensure the tool can scale with your growing cloud infrastructure and handle the performance requirements of your organisation. Look for features such as distributed architecture, auto-scaling capabilities, and high availability to ensure reliability and performance under load.
Top 15 Best Cloud Security Tools in 2025
It is important to vet your options when choosing a tool that is protecting your cloud environment. Following is a list of the best cloud security tools in 2025 that will protect your sensitive business data stored on cloud infrastructure.
ZeroSpam
ZeroSpam is a cloud-based email security solution designed to protect organisations from email-based threats such as phishing, malware, and spam.
Pros:
- Provides robust protection against email-based threats.
- Offers easy setup and management through a cloud-based platform.
- Includes features such as email filtering, anti-phishing, and attachment scanning.
Cons:
- May require additional integration with other security tools for comprehensive protection.
- Pricing structure may not be suitable for all organisations.
Barracuda CloudGen Firewall
Barracuda CloudGen Firewall is a cloud-based network security solution that provides firewall protection, VPN connectivity, and advanced threat protection for cloud environments.
Pros:
- Offers comprehensive network security features, including firewalling, intrusion prevention, and VPN capabilities.
- Provides centralised management and visibility across cloud and on-premises environments.
- Integrates with cloud platforms and third-party security solutions for enhanced protection.
Cons:
- May require additional licensing for advanced features, leading to increased costs.
- Deployment and configuration may be complex for organisations with limited technical expertise.
CrowdStrike Falcon
CrowdStrike Falcon is a cloud-native endpoint security platform that uses AI-driven threat intelligence to protect endpoints from advanced threats and malware.
Pros:
- Utilises advanced AI and machine learning algorithms for threat detection and prevention.
- Offers real-time visibility and response capabilities across endpoints and cloud workloads.
- Provides cloud-based management and scalability for large-scale deployments.
Cons:
- May have a steep learning curve for organisations new to cloud-native security solutions.
- Requires continuous updates and tuning to maintain effectiveness against evolving threats.
Datadog Cloud Security Management
Datadog Cloud Security Management is a cloud-based security platform that provides real-time threat detection, compliance monitoring, and security analytics for cloud environments.
Pros:
- Offers comprehensive security monitoring and compliance management capabilities.
- Provides real-time visibility into cloud infrastructure and applications.
- Integrates with popular cloud providers and security tools for seamless deployment and management.
Cons:
- May require customisation to meet specific security and compliance requirements.
- Pricing may be prohibitive for small to mid-sized organisations with limited budgets.
Splunk Enterprise Security
Splunk Enterprise Security is a SIEM (Security Information and Event Management) platform that provides security monitoring, threat detection, and incident response capabilities for cloud and on-premises environments.
Pros:
- Offers advanced correlation and analytics capabilities for detecting and investigating security threats.
- Provides customisable dashboards and reports for security visibility and compliance reporting.
- Integrates with a wide range of security tools and data sources for comprehensive threat detection.
Cons:
- May require significant resources for deployment and configuration.
- Complexity of the platform may require specialised training for effective use.
Bitglass: Total Cloud Security
Bitglass Total Cloud Security is a cloud access security broker (CASB) solution that provides data protection, threat protection, and access control for cloud applications and services.
Pros:
- Offers comprehensive cloud security features, including data loss prevention (DLP), threat intelligence, and access control.
- Provides visibility and control over cloud usage and data sharing activities.
- Supports integration with leading cloud providers and SaaS applications for seamless protection.
Cons:
- May require careful configuration to avoid impacting user productivity.
- Pricing structure may be complex, with additional costs for advanced features and functionality.
CloudKnox
CloudKnox is a cloud security platform that focuses on identity and permissions management, helping organisations enforce least privilege access policies and reduce the risk of data breaches.
Pros:
- Offers granular visibility and control over permissions across cloud environments.
- Provides automated policy enforcement and anomaly detection to identify and mitigate security risks.
- Integrates with identity providers and cloud platforms for seamless deployment and management.
Cons:
- May require significant effort to configure and maintain least privilege access policies.
- Integration with existing identity management solutions may be challenging for some organisations.
Cyscale
Cyscale is a cloud security posture management (CSPM) platform that helps organiations assess, monitor, and remediate security risks in cloud environments.
Pros:
- Offers comprehensive cloud security assessment and compliance management capabilities.
- Provides continuous monitoring and alerting for security misconfigurations and vulnerabilities.
- Integrates with cloud providers and security tools for seamless security management.
Cons:
- May lack some advanced security features found in other CSPM solutions.
- User interface and workflow may require improvement for ease of use.
Delinea
Delinea is a cloud-native security platform that offers identity and access management (IAM), privileged access management (PAM), and secrets management capabilities for cloud environments.
Pros:
- Provides centralised identity and access management for cloud resources and applications.
- Offers robust privilege management features, including credential rotation and session monitoring.
- Integrates with leading cloud providers and IAM solutions for seamless deployment and management.
Cons:
- May require additional customisation for specific use cases and integration requirements.
- Pricing structure may be complex, with additional costs for advanced features and functionality.
Orca Security
Description: Orca Security is a cloud security platform that provides comprehensive visibility and protection for cloud assets, workloads, and data using agentless, deep-scanning technology.
Pros:
- Offers agentless deployment and deep-scanning technology for comprehensive cloud security.
- Provides continuous monitoring and risk assessment for cloud assets and resources.
- Integrates with leading cloud platforms and security tools for seamless deployment and management.
Cons:
- May require careful configuration and tuning to avoid impacting cloud performance.
- Advanced features may require additional licensing or subscription fees.
HashiCorp Vault
HashiCorp Vault is a cloud-native secrets management platform that helps organisations secure, store, and control access to sensitive data, credentials, and API keys in cloud environments.
:Pros
- Provides centralised secrets management and encryption for cloud resources and applications.
- Offers dynamic secrets generation, rotation, and revocation to enhance security posture.
- Integrates with leading cloud providers and CI/CD pipelines for seamless deployment and automation.
Cons:
- May require specialised expertise to deploy and configure effectively.
- Advanced features may require additional customisation and integration effort.
Trend Micro Cloud One
Trend Micro Cloud One is a cloud security platform that provides a suite of security services, including workload protection, container security, file storage security, and network security for cloud environments.
Pros:
- Offers comprehensive cloud security services to protect workloads, containers, files, and networks.
- Provides centralised management and visibility across multiple cloud platforms and environments.
- Integrates with leading cloud providers and security tools for seamless deployment and management.
Cons:
- May have a complex pricing structure with additional costs for specific services and features.
- Integration with existing security tools and workflows may require additional effort and configuration.
Palo Alto Networks Prisma Cloud
Palo Alto Networks Prisma Cloud is a cloud security platform that provides comprehensive security for cloud-native applications, workloads, and infrastructure across multi-cloud environments.
Pros:
- Offers full-stack security for cloud-native applications, including runtime protection, vulnerability management, and compliance monitoring.
- Provides real-time visibility and control across multiple cloud platforms and environments.
- Integrates with DevOps tools and CI/CD pipelines for seamless security integration and automation.
Cons:
- May have a steep learning curve for organisations new to cloud-native security solutions.
- Advanced features may require additional licensing or subscription fees.
McAfee MVISION Cloud
McAfee MVISION Cloud is a cloud access security broker (CASB) solution that provides data protection, threat prevention, compliance management for cloud services and google cloud consultancy.
Pros:
- Offers comprehensive cloud security features, including data loss prevention (DLP), threat detection, and compliance management.
- Provides real-time visibility and control over cloud usage and data sharing activities.
- Integrates with leading cloud providers and SaaS applications for seamless protection.
Cons:
- May require careful configuration to avoid impacting user productivity.
- Pricing structure may be complex, with additional costs for advanced features and functionality.
Symantec CloudSOC
Symantec CloudSOC is a cloud security platform that provides threat protection, data loss prevention (DLP), and compliance monitoring for cloud applications and services. They also serve as a aws professional services consultant.
Pros:
- Offers advanced threat protection capabilities, including real-time monitoring and incident response.
- Provides data loss prevention (DLP) features to prevent the unauthorised disclosure of sensitive information.
- Integrates with leading cloud providers and security tools for seamless deployment and management.
Cons:
- May have a complex pricing structure with additional costs for specific services and features.
- Integration with existing security tools and workflows may require additional effort and configuration.
Conclusion
Data privacy is a fundamental right of businesses and consumers alike in the digital age making it essential to safeguard it from potential breach. If you are wondering whether you need the best cloud security tool for your organisation, FuturByte will help you conduct an audit and suggest the best cloud security tool suited to your requirements. We not only offer services such as Azure managed service providers but also help you create serverless web applications. Contact us for a free consultation.
Looking for Cloud Migration Solutions?
Connect with Expert Cloud Developers

Frequently Asked Questions
Cloud security tools are software solutions designed to protect cloud environments, data, applications, and workloads from cyber threats, unauthorised access, and data breaches. These tools offer various features such as threat detection, encryption, access control, and compliance management to ensure the security and integrity of cloud-based assets.
Cloud security is important because organisations are increasingly adopting cloud computing services to store, process, and manage their data and applications. However, the cloud environment introduces new security challenges and risks, including data breaches, malware attacks, and misconfigurations.
Common features of the best cloud security tools include threat detection and prevention, data encryption, access control, security monitoring, compliance management, and incident response. These features work together to protect cloud environments from a wide range of security threats and vulnerabilities.
Have questions or feedback?
Get in touch with us and we‘l get back to you and help as soon as we can!